Situation: I have created a new Twitter account for a business I am managing. Twitter wants to verify the email address I’ve used, so I get an email asking me to click a link.
I am using my mobile phone. It’s a Nexus 4 – new and fast, with a full-featured browser on board.
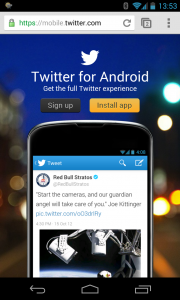
I tap the link on my phone, and after a few redirects I end up at this page:
Note the URL – it’s simply mobile.twitter.com. The validation code provided in the email has been stripped. No matter what I click, I can’t succeed. Worse, this page bears absolutely no resemblance to what I was hoping or expecting to get. I don’t want the app and I’ve already signed up (it also doesn’t scroll – there’s nothing below the screen fold).
So, it seems I cannot validate my email address from a mobile phone. Or Twitter doesn’t want me to. Either way, I can’t perform a quite straightforward task.
You might be aware that in Chrome there is an option ‘Request Desktop Site’ which re-requests the page but pretends the phone is a desktop. Unsurprisingly, the full-featured Twitter homepage is reloaded. Unfortunately Chrome doesn’t retain this setting between tabs so simply going back and re-tapping the email doesn’t work. You need to copy/paste the URL into the current tab.
With that little dance, it works. My email is validated.
Of course, it always should have worked. This is a trivial exercise and the modern smartphone is more than capable of this activity. Instead, the website operator insists on using a brutal, unhelpful redirect. What an utterly poor experience for such a simple task.